The Secondary zone type
The secondary zone type makes Posadis a secondary DNS server for the zone (see Authoritative DNS).
As a secondary DNS server, Posadis can also accept DNS Update messages: it will forward them to the masters for the zone, as set by the masters configuration option. If DNS update message are not signed, the master DNS server should also be set to accept DNS update queries sent by the secondary DNS server, if this update forwarding is desired. In this case, it’s very important to restrict the clients from which DNS update messages are accepted by the secondary (using update_acl), since if the message is forwarded, the primary DNS server can no longer do the check itself.
If the master server from which the zone is transferred is a multi-homed host (i.e., it has multiple internet IP numbers), special care needs to be taken to make sure DNS Notify messages work. You’ll usually want to specify only one of the IP addresses as the address to get zone transfers from, so to make sure we still accept notifications from the other IP addresses, you should list them in the allow_notify_from list. This makes sure the master is not tried twice for zone transfers, but its notify messages are always accepted by the secondary regardless of what IP address of the master they happened to come from.
Configuration options
The following configuration options are available:
- masters (list of IP numbers) - DNS servers the server will attempt to get a zone transfer from. These servers will be tried in order. Also, the zone accepts notify messages, that tell the server to re-load the zone, from these masters. This needs to be set for the zone to work correctly.
- allow_notify_from (access control list) - Alternate sources from which we trust DNS Notify messages (see Authoritative DNS); mainly useful for multi-homed hosts, as noted above. Defaults to
none.
- slaves (list of IP numbers) - List of slaves for the zone. Slaves get notification when the zone changes, and zone transfers are always allowed to them. Defaults to
none.
- xfr_acl (access control list) - Determines who further to allow zone transfers to. By default, zone transfers are allowed to all listed nameservers that are in zone, i.e. all domain names in the zone
NSrecord that are in the zone itself. You can revert this behavior by adding the special keyword nons to the address match list.
- update_acl (access control list) - Determines who to accept DNS update messages from. Defaults to
none.
Examples
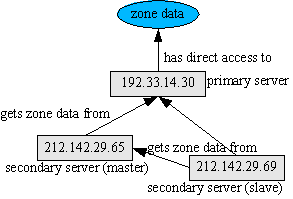
Taking the scenario discussed in Authoritative DNS:
A simple example for the acdam.net.znf file on could be:
zone secondary masters slaves update_acl 127.0.0.1
In this case, the secondary gets its zone from , and can transfer it to . It also accepts DNS update messages from the local host. On the other hand, the configuration on might look something like:
zone secondary masters ,
This DNS server does not do zone transfers itself; it gets its own copy from the two other DNS servers.
![[Posadis logo]](/images/posadis-logo.png)